We use cookies on this site to provide you with the best experience.
How we take care about your security
- Authentication of Internet banking server
We use SSL cryptographic protocol for a secure connection between the customer and the server and protection against the attacks aimed at replacing the banking Web server and information modification during transfer.
- The use of group of two or more signatures for the formatting of electronic settlement document
In order to minimize fraudulent actions with the customers’ accounts by third parties if one of EDS keys is lost or compromised, the use of group signature mechanism is recommended. In such a case, only the payment documents that contain a full group of signatures and coincide with the signature in the card of signature samples will be processed.
- Authentication of Internet banking users
We use two-factor authentication for secure access to the system. In order to log in to the system, personal (secret) cryptographic key must be available and the password must be entered.
Please pay attention that only you possess the secret key.
- Data transfer confidentiality
In order to ensure the confidentiality of the data, which users exchange with the bank via Internet banking channels, this data is encrypted. Thus, interception and unauthorized reading of payment and other information is ruled out.
- Payment document authorization
We use electronic digital signature (EDS) mechanism to confirm authorship and integrity of electronic payment documents. The validity of EDS is checked before any document processing operation.
- The use of USB-token (eToken) as an electronic key medium
In order to ensure reliable storing and use of reliable keys, the use of hardware signature generation devices (tokens) is recommended. This ensures the saving of the personal key in the protected memory and the execution of cryptographic operations in a way preventing the copying of the personal key or its finding outside the protected memory of the device.
Do not leave your USB token unattended!
- Restriction of the list of ІР addresses/ІР subnetworks during access to Internet banking
You may set the restriction on the list of IP addresses and/or IP subnetworks, from which Internet banking system may be accessed (if the system is accessed from a static ІР address or a range of addresses – this can be clarified with your provider). Access from other addresses except the defined ones will be blocked.
The setting guidelines are available at the link (“User administration guidelines” file)
Account security may be under threat without proper protection on the user’s part

Comply with these rules for secure work in the system
Daily analyze all the messages on electronic settlement documents accepted or not accepted by the bank and notify the bank immediately on the cases of unauthorized funds crediting (transfer)!
Connect SMS with a digital password (ОТР passwords) for additional confirmation of actions and operations in the system (“two-factor authentication”).
You may connect notifications on:
- login confirmation;
- UAH payments confirmation;
- key activation;
- electronic signature (informational);
- notification on log in to the system (informational).
Guidelines are available at the link.
When connecting to the Internet banking system website (https://rbo.raiffeisen.ua/ibank/home?1) check the address attentively (the first symbols of the address must be https://, and not http://).
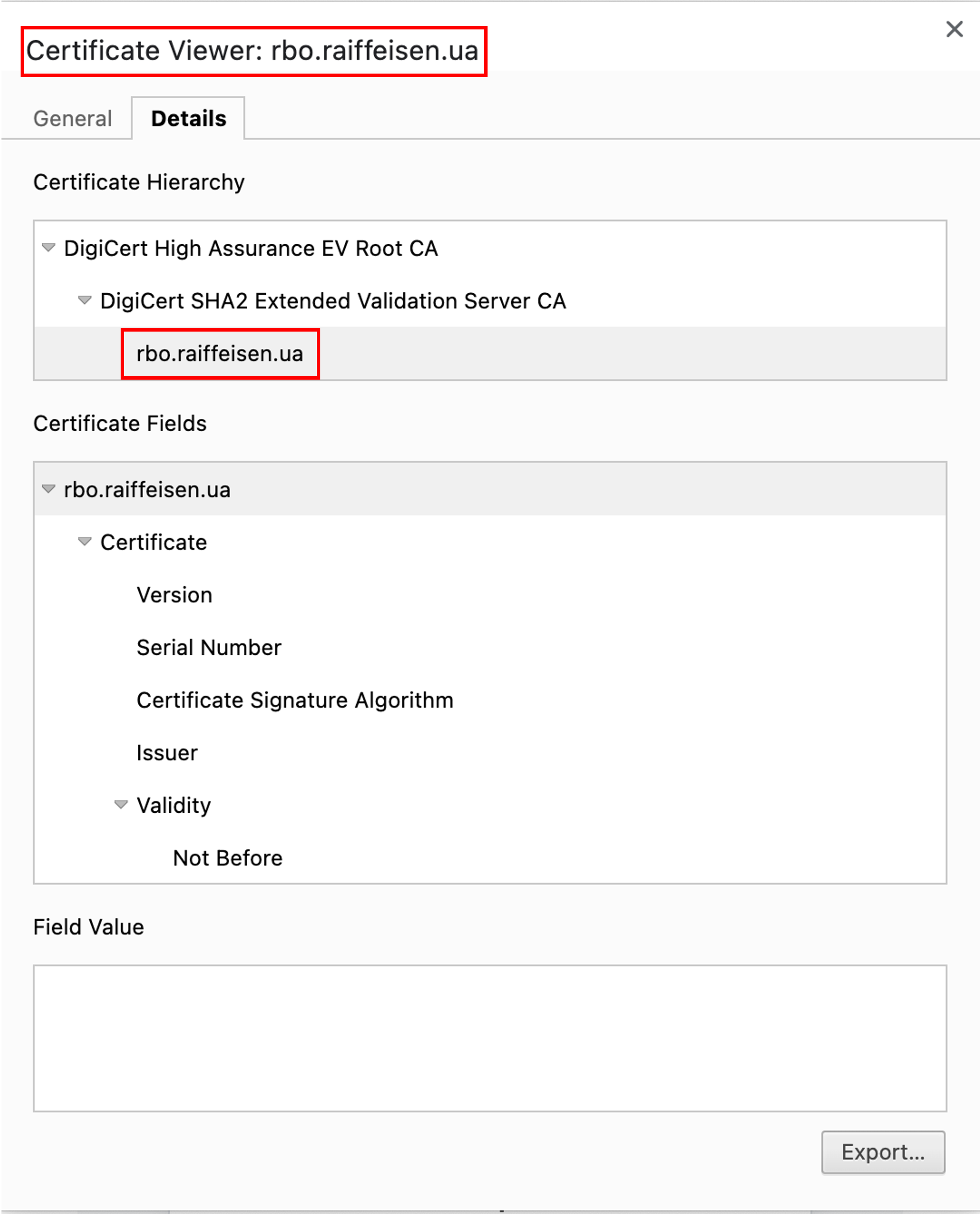
You should also pay attention to the website certificate.
The certificate can be viewed by pressing the “lock” symbol before the website address – “lock” – connection is secure – the certificate is valid
Install antivirus software (SW), antispyware and a firewall on your workstation.
Please pay attention that the software must be licensed, installed from reliable official sources. Otherwise, the probability of the workstation infection with viruses or a malicious code exists.
Timely update the system software and the PC operation system.
During access to the Internet banking system, work in the operation system with a user account having extended rights in the system, e.g. Administrator, is strongly discouraged.
The personal key and password are the most critical data in terms of secure work in the Internet-banking system.
The Bank under no circumstances has access to the users’ personal keys.
Use hardware devices (tokens) for storing keys. If the key is stored in a file container, the keys must be on a removable information medium (such as USB stick) exclusively. Even temporary storing of the EDS keys on a hard drive is not allowed.
Change the password for access to the key from time to time. The password must be reliable: use lowercase and uppercase letters, digits and special symbols. The minimum password length is 12 symbols. Avoid the combinations that are easily guessed.
A medium with a valid key (mobile information medium, token) must be under the user’s personal control.
Do not transfer the key information medium (token) and/or do not disclose the password thereto to other persons, including the bank employees, under any circumstances.
The access password (PIN code) to personal keys must not be stored in open form (e.g., be written on paper) and must not be used for other systems and services. The same concerns the blocking word.
Do not leave the key information medium (token) connected to a PC if the work in the system is suspended or not carried out, the PC is used to execute other functions, as well as on non-working hours.
If users are dismissed or transferred to other positions not involving the work in the Internet-banking system, their keys must be blocked immediately.
In the event of compromising or suspected compromising of a key (the loss, damage to the key information medium, disclosure of a password or other events and/or actions that resulted or may result in unauthorized key use), the compromised key must be blocked urgently as follows:
а) you may do it in the system yourself (log-in to the system, block or reissue your key in the profile), this can also be done via the Mobile application
b) call the Support Service of Raiffeisen Business Online (0 800 505 770), mention your secret blocking word and your key will be blocked immediately
Avoid connections to the system websites from the PCs not controlled by you and not reliable (e.g., in the internet cafes, hotels, etc.) at the banner link or a link received via email. It is better to enter the website address in the browser and add it to the browser bookmarks.
Perpetrators may commit phishing attacks by email and/or in social networks to get the system’s user authentication data.
The key methods of taking possession of the key information include:
- sending users forged emails, notices with a link to the website address masked as the bank’s address;
- distribution of the software with malicious code via emails, social networks or websites;
- unauthorized remote management of a user’s PC by means of remote access.
The Bank shall under no circumstances send emails, SMS or social network messages with a request for the key, password, following via the specified email address, neither shall it distribute computer applications by means of email.
User shall be responsible for the keeping of keys and passwords.
If you receive such letters, applications or any messages by email, inform the bank about it urgently.

















